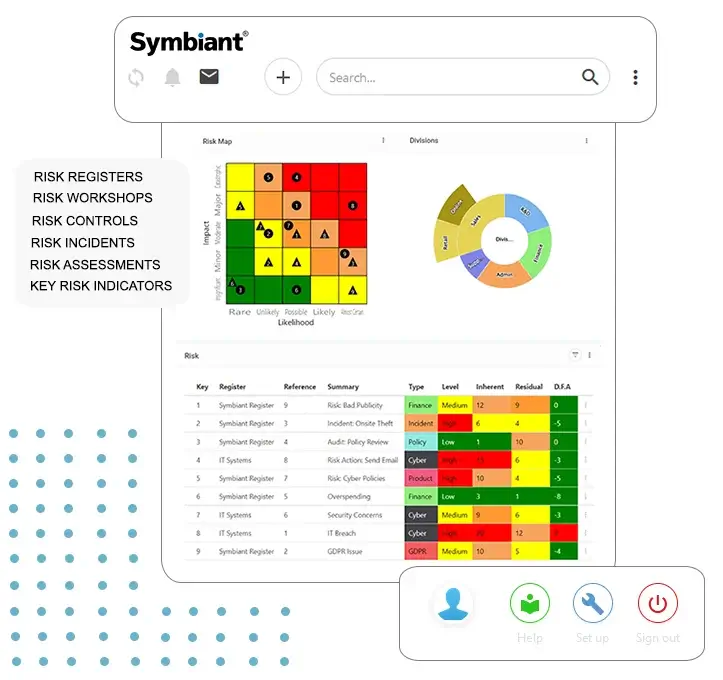
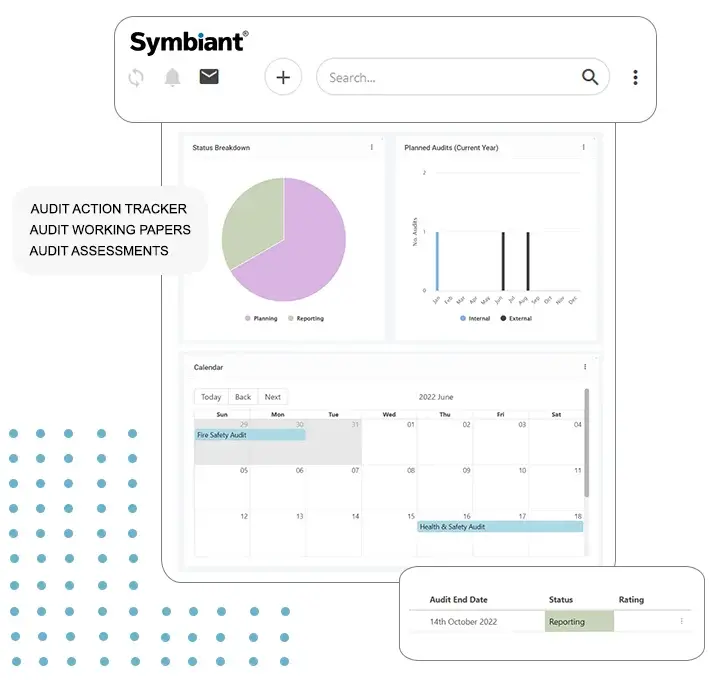
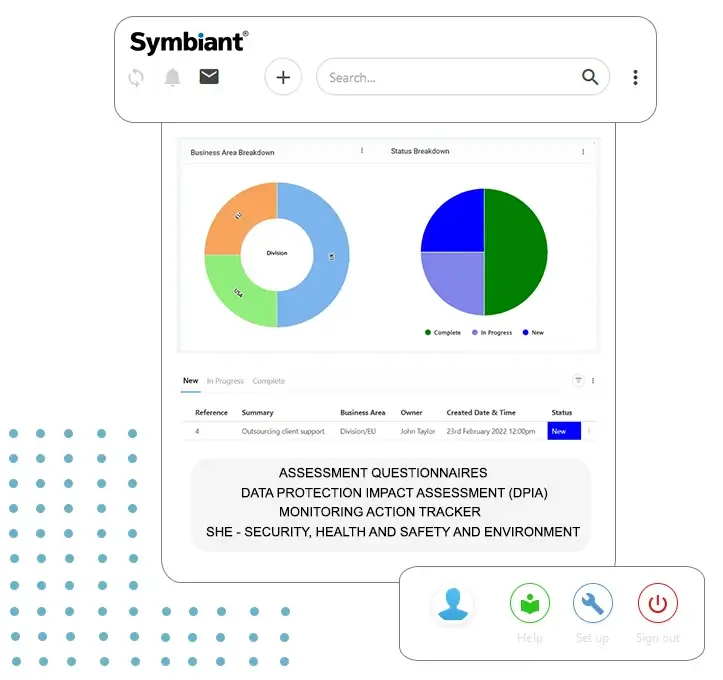
Introduction
What is the Audit Trail Concept, and what do you need to know?
An Audit Trail is a chronological record of events, activities, or changes within a system, process, or organisation.
It provides a detailed and documented history of these events, allowing for tracking, monitoring, and verifying activities over time.
The concept of an audit trail is commonly used in various industries and contexts, particularly those that require accountability, transparency, security, and compliance. For example, industries such as Food Safety, Aged Care, Financial, and Manufacturing require more regular audits to ensure compliance and ongoing success.
But what is an audit trail? Let’s discuss the critical parts of an audit trail first.
Key Parts of An Audit Trail
Firstly, we’ll discuss what makes up an audit trail. This is one of the many areas you’ll need to know to understand the Audit Trail Concept.
- Timestamps: Each recorded event includes a timestamp that indicates its occurrence time. This chronological ordering of events helps establish the sequence of activities.
- User Identification: The audit trail records the identity of the users or entities responsible for each event. This is crucial for accountability and determining who performed specific actions.
- Event Descriptions:
- Event descriptions provide detailed explanations of the actions or changes during the events. This description provides context and clarity about the recorded activity.
- System Information: Additional technical details about the event, such as the location, source, and type of activity, might be included. This information aids in understanding the event’s context.
Audit trails involve collecting and storing these various data sources, also called data tracking. However, in doing so, it raises concerns about Data Security.

The Importance of Data Security and Tracking
Data Security
Data security protects digital information from unauthorised access, use, disclosure, disruption, modification, or destruction.
Ensuring data is secure is vital for:
- Privacy Protection
- Regulatory Compliance
- Business Continuity
- Intellectual Property Protection
- Prevention of Cyberattacks
Data Tracking
However, data tracking involves collecting and analysing information about user behaviour, interactions, preferences, and more. Businesses often use this information to enhance services, focus marketing efforts, and make informed decisions.
There are various uses for tracked data:
- Personalisation
- Business insights
- Marketing efficiency
- User Experience improvement
- Product Development
Balancing Data Security and Tracking
While data security and tracking offer significant benefits, it’s crucial to strike a balance between the two. Stricter data security measures may limit the potential for data breaches, but overly restrictive measures could hinder data-tracking efforts. Conversely, robust data tracking can improve user experiences and business outcomes, but businesses must undertake it while respecting user privacy and complying with regulations. Therefore, finding a balance is necessary for data tracking that ensures user privacy. There are countless ways of achieving this, and every business will do so differently.
Some ways of protecting user privacy while allowing data tracking are:
- Anonymising the user data – giving the user a number or another unique identifier means their data is identifiable, but the user remains anonymous.
- Having the data be need-to-know, limiting the access to the data only to show what they need.
- Giving users the ability to view their data.
But if data security and privacy are essential, why must we track the data and maintain audit trails?

Reasons Behind Maintaining Audit Trails
Detecting Unauthorised Access:
Audit trails are crucial for identifying and preventing unauthorised access to systems, applications, and sensitive data. Unauthorised access can lead to security breaches, data theft, and other malicious activities.
There are several way to use audit trails to detect unauthorised access:
- Recording User Activity: Every time a user interacts with a system or application, the audit trail captures details such as user identity, timestamp, and the actions performed. This comprehensive record enables the identification of any unusual or suspicious behaviour.
- Real-time Monitoring: Security teams can monitor audit trail data in real-time, promptly detecting and responding to unauthorised access attempts. Administrators can set up alerts to notify them when specific predefined events occur.
- Pattern Recognition: By analysing historical audit trail data, security personnel can identify patterns of behaviour that deviate from the norm. For instance, repeated failed login attempts or access from unusual locations can indicate unauthorised access.
Monitoring Changes and Edits:
Audit trails are essential for tracking data, configurations, and settings modifications. This is crucial for maintaining data integrity, ensuring accountability, and facilitating troubleshooting.
Monitoring changes can be aided by audit trails in several ways:
- Recording Changes: Any time data is modified, edited or deleted, the audit trail captures the details of the change, including who made the change and when it occurred. This is invaluable for identifying the source of errors or inconsistencies.
- Version Control: Audit trails provide a clear history of system changes where multiple versions of documents or files exist. This makes it easier to roll back to previous versions or trace the evolution of a copy.
- Accountability: Having a record of changes promotes accountability among users and administrators. When specific individuals are tied to changes, there is a greater responsibility for maintaining accurate and secure data.
Meeting Compliance Requirements:
Many industries and organisations are subject to regulatory and legal requirements that mandate the maintenance of audit trails. Compliance with these requirements is essential to ensure data protection, security, and transparency.
Audit trails can facilitate compliance by:
- Evidence for Audits: Regulatory bodies and auditors often require organisations to demonstrate adherence to industry standards and regulations. Audit trails provide a transparent and verifiable record of user activity, serving as evidence of compliance.
- Data Protection and Privacy: Regulations like GDPR, HIPAA, and CCPA require organisations to protect sensitive data and provide individuals with control over their data. Audit trails demonstrate that data is accessed, processed, and stored in compliance with these regulations.
- Transparency: An organisation that maintains thorough audit trails demonstrates transparency in its operations. Customers, stakeholders, and regulatory authorities can review these records to ensure the organisation follows ethical and legal practices.
Now that we understand the reasons for maintaining audit trails, we can explore precisely how to create them.

Methods For Creating Audit Trails
Log Files:
Log files are standard for creating audit trails in various software applications and systems. They record a chronological sequence of events, actions, and transactions. Log files can capture a wide range of information, including user activities, system events, errors, etc.
This is how log files are employed in the creation of audit trails:
- Event Recording: Software applications and systems generate log entries for significant events, such as user logins, file accesses, data changes, and system errors.
- Structured Information: Log files typically contain structured data, including timestamps, user IDs, action descriptions, and other relevant details. This structured data makes it easier to analyse and interpret the audit trail.
- Real-time Monitoring: Security personnel can monitor log files in real-time to detect unauthorised access attempts, suspicious activities, and anomalies.
- Analysis and Forensics: Log files are essential for post-incident analysis and forensics. They help identify the root causes of issues, track the sequence of events, and understand the context of security incidents.
Next, we’ll discuss how Database Triggers can help create audit trails.
Database Triggers:
Database triggers are mechanisms that automatically execute a predefined action (such as recording an entry in an audit trail) when specific events occur within a database. They are often used to track changes in database records and maintain an accurate record of data modifications.
Here’s how database triggers create audit trails:
- Change Tracking: Database triggers are set up to fire when certain events occur, such as an INSERT, UPDATE, or DELETE operation on a table.
- Immediate Recording: When a relevant database event occurs, the trigger is activated, and it adds an entry to the audit trail with details about the change, user, timestamp, and other relevant information.
- Data Integrity: Database triggers help ensure the integrity of the audit trail because they are automatically triggered by database operations, reducing the risk of oversight or omission.
- Transaction Context: Database triggers can capture additional contextual information, such as the transaction ID and session information, which can be valuable for understanding the context of changes.
Blockchain Technology:
Blockchain technology is a decentralised and distributed ledger system that records transactions securely and transparently. While often linked with cryptocurrencies, it can also generate tamper-resistant audit trails for various applications:
- Immutable Records: In a blockchain, once a transaction is added to the ledger, it cannot be altered or deleted. This immutability ensures the integrity of the audit trail.
- Decentralisation: A blockchain operates on a decentralised network of nodes, reducing the risk of a single point of failure and increasing the audit trail’s overall security.
- Transparency: All participants in the blockchain network can access and verify the records, promoting transparency and trust.
- Smart Contracts: Blockchain platforms often support smart contracts, which can automate certain actions when specific conditions are met. These contracts can trigger audit trail entries based on predefined rules.
- Proof of Existence: Blockchain audit trails provide proof of the existence and authenticity of data at a specific point in time, which can be helpful in legal and regulatory contexts.
Finally, we’ll discuss how to get started with audit trails.
Best Practices for Starting an Audit Trail
Deciding What to Log:
- Identify Objectives: Begin by defining the objectives and goals of your audit trail. What are you trying to achieve? Is it primarily for security, compliance, troubleshooting, or all of these? Clearly defining your objectives will help you determine what needs to be logged.
- Regulatory Requirements: Consider any industry-specific regulations or compliance standards for your organisation. These regulations may mandate specific types of data that must be logged. For instance, HIPAA may require logging of healthcare-related data access.
- Risk Assessment: Conduct a risk assessment to identify potential security threats and vulnerabilities in your systems. Focus on the areas where unauthorised access or data breaches are most likely to occur.
- Data Sensitivity: Categorise your data based on sensitivity. High-risk data, such as personal or financial information, should have more comprehensive audit logs than low-risk data.
- User Roles and Privileges: Audit logs should reflect user roles and privileges. Determine what actions are permissible for each user role and ensure that the logs capture these actions.
- Critical Systems and Assets: Prioritise auditing for critical systems, assets, and applications. Breaches or unauthorised access can have the most significant impact in these areas.
- Consult with Stakeholders: Involve key stakeholders, including IT, legal, and compliance teams, in the decision-making process to ensure that all relevant perspectives are considered.
Specifying Detail Levels:
- Granularity: Decide on the level of granularity for your audit trail. This involves determining how detailed your logs should be. A high level of detail may be necessary for some actions, while a more summarised log entry for others may suffice.
- Retention Period: Define how long you will retain audit logs. This can vary based on regulatory requirements, internal policies, and storage capacity. More extended retention periods may be necessary for compliance purposes.
- Event Types: Specify the events and actions that should be logged. Examples can include user logins, file access, data changes, system configuration changes, and security-related events (e.g., failed login attempts).
- Timestamps: Ensure that timestamps are accurate and synchronised across your systems. Timestamps are critical for establishing the sequence of events in an audit trail.
- User Identification: Capture user identification information, such as usernames or unique identifiers, to attribute actions to specific users.
- Contextual Data: Include contextual data in audit logs to provide additional event information. This might include the IP addresses, devices used or users’ locations.
- Alerts and Notifications: Set up alerts and notifications for specific events that require immediate attention, such as repeated failed login attempts or access to sensitive data.
- Log Integrity: Implement measures to ensure the integrity of your audit logs. Protect them from tampering and consider using encryption or digital signatures for added security.
By carefully considering these best practices, organisations can establish effective audit trails that meet their specific objectives, comply with regulations, and enhance overall security and accountability. It’s essential to regularly review and update your audit trail policies as your organisation evolves and as new threats and compliance requirements emerge.
Conclusion
In conclusion, audit trails are a recommended practice and an indispensable component of modern data management and security. They serve as the digital breadcrumbs that help organisations trace and understand the who, what, when, and why of critical events within their systems. Audit trails also play a pivotal role in establishing and maintaining trust within an organisation and with external parties.
Audit Trails are the cornerstone of accountability in the digital age. Knowing that a system is equipped with comprehensive audit trails instils trust. With Symbiant’s Audit Software, users can be confident that their interactions and data are monitored and protected. When reliable audit trail data inform decisions, stakeholders have greater confidence in the choices made by organisations. It demonstrates that decisions are based on evidence and facts.
Finally, audit trails are not merely a technical necessity but a strategic asset. They foster trust and accountability, two pillars of successful organisations. By recognising their importance and implementing best practices, organisations can enhance their security, compliance, and overall integrity, strengthening their relationships with stakeholders and ensuring their continued success.
References
Audit Logging Overview, DataDog, 2022
What is an Audit Trail & How Are Audit Trails Used in Business? Barbara Cook, Tipalti, 2022
Audit trails: Everything you need to know, Mercy Johny, Zoho, 2022
Data Tracking: What Is It and What Are the Best Tools, Kristen Baker, Hubspot, 2021
Why Data Monitoring is Key to Sensitive Data Protection, Peter Keough, Immuta, 2023